Delving into the realm of securing health data with cloud technology unveils a crucial aspect of modern healthcare practices. From encryption methods to compliance regulations, this guide explores the intricate details essential for safeguarding sensitive information in the digital age.
Importance of Data Security in Healthcare
Ensuring data security in the healthcare sector is of utmost importance due to the sensitive nature of the information involved. Health data contains personal and confidential details about patients, making it crucial to protect this data from unauthorized access or breaches.
Risks Associated with Inadequate Data Security
- Unauthorized Access: Without proper security measures, hackers may gain access to patient records, leading to identity theft or fraud.
- Data Breaches: Inadequate security can result in data breaches, exposing sensitive information to malicious actors who may misuse it.
- Ransomware Attacks: Healthcare organizations are often targeted by ransomware attacks, where hackers encrypt data and demand a ransom for decryption.
Consequences of a Data Breach in Healthcare
- Legal Ramifications: Data breaches can lead to hefty fines and legal consequences for healthcare organizations that fail to protect patient information.
- Damage to Reputation: A breach can tarnish the reputation of a healthcare provider, eroding patient trust and confidence in the organization.
- Patient Harm: In some cases, data breaches can result in patient harm if their medical information is accessed or altered by unauthorized individuals.
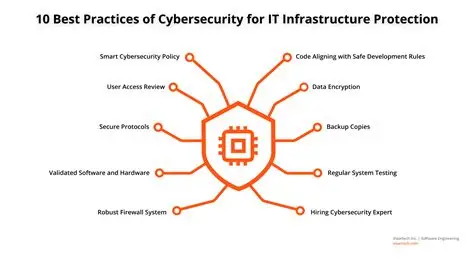
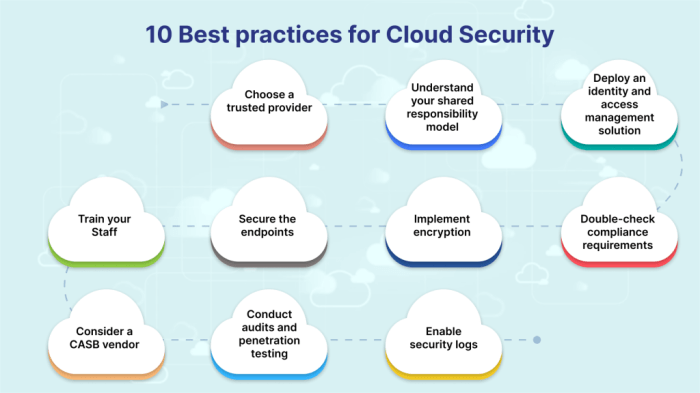
Best Practices for Securing Health Data in the Cloud
In the healthcare industry, the security of patient data is of utmost importance. With the increasing use of cloud technology, it is crucial to implement best practices to ensure the confidentiality, integrity, and availability of health data.
Encryption Methods for Protecting Health Data
Encryption plays a vital role in safeguarding health data in the cloud. By converting sensitive information into a coded format that can only be accessed with the right decryption key, encryption helps prevent unauthorized access. Some common encryption methods include:
- Use of Advanced Encryption Standard (AES) for encrypting data at rest and in transit.
- Implementing Transport Layer Security (TLS) to secure data communication between systems.
- Utilizing Public Key Infrastructure (PKI) for secure key management and authentication.
Access Control Mechanisms to Limit Unauthorized Access
Controlling access to health data is essential to prevent unauthorized users from viewing or manipulating sensitive information. Access control mechanisms help limit access based on user roles, permissions, and other factors. Some best practices include:
- Implementing role-based access control (RBAC) to assign specific permissions to users based on their roles within the organization.
- Enforcing strong authentication methods such as multi-factor authentication (MFA) to verify user identities.
- Auditing access logs regularly to monitor and track user activities within the system.
Importance of Regular Data Backups and Disaster Recovery Plans
Regular data backups and disaster recovery plans are crucial for ensuring the availability and integrity of health data in case of unexpected events such as cyberattacks, system failures, or natural disasters. Some key practices to consider include:
- Performing regular backups of health data to secure offsite locations to prevent data loss.
- Testing data restoration processes to ensure quick recovery in case of data loss or system downtime.
- Developing a comprehensive disaster recovery plan that Artikels steps to be taken in the event of a data breach or system failure.
Compliance Regulations for Health Data in the Cloud
When it comes to storing and securing health data in the cloud, organizations must comply with various regulations to ensure the protection of sensitive information. One of the key regulations that govern the storage and security of health data is the Health Insurance Portability and Accountability Act (HIPAA).
HIPAA sets the standard for protecting sensitive patient data and requires organizations to implement certain safeguards to secure this information.
HIPAA Compliance
- Organizations handling health data in the cloud must ensure that their systems and processes adhere to HIPAA regulations.
- They should implement appropriate technical safeguards, such as encryption and access controls, to protect data stored in the cloud.
- Regular risk assessments and audits should be conducted to identify and address any vulnerabilities in the system.
- Employee training on HIPAA regulations and best practices for data security is essential to maintain compliance.
Role of Auditing and Monitoring
- Auditing and monitoring play a crucial role in maintaining compliance with regulations like HIPAA.
- Regular audits help organizations identify any gaps in their security measures and address them promptly.
- Monitoring access to health data in real-time can help detect unauthorized activities and prevent data breaches.
- Organizations should have systems in place to log and track all access to health data to ensure compliance with regulatory requirements.
Secure Infrastructure and Architecture
When it comes to securing health data in the cloud, having a robust infrastructure and architecture is crucial. These elements form the foundation for a secure environment that protects sensitive information from cyber threats.
Best Infrastructure Practices for Securing Health Data in the Cloud
- Implementing strong encryption protocols to safeguard data both in transit and at rest.
- Regularly updating security patches and software to address any vulnerabilities.
- Utilizing multi-factor authentication to add an extra layer of protection for accessing data.
- Restricting access based on the principle of least privilege to ensure only authorized personnel can view or modify data.
Importance of Network Segmentation in a Healthcare Cloud Environment
Network segmentation involves dividing a network into smaller segments to limit the spread of cyber threats. In a healthcare cloud environment, this practice is crucial for isolating sensitive health data and preventing unauthorized access.
How a Secure Architecture Can Mitigate Cybersecurity Threats
- Implementing firewalls and intrusion detection systems to monitor and block malicious activities.
- Utilizing virtual private networks (VPNs) to create secure connections for remote access to data.
- Regularly conducting security audits and assessments to identify and address any vulnerabilities in the architecture.
- Employing role-based access control to ensure that only authorized users can perform specific actions within the system.
Final Thoughts
In conclusion, prioritizing the security of health data in the cloud is paramount for maintaining patient confidentiality and organizational integrity. By implementing the best practices Artikeld here, healthcare providers can navigate the complexities of data security with confidence and diligence.
Questions Often Asked
What are the common risks associated with inadequate data security in healthcare?
Inadequate data security can lead to unauthorized access, data breaches, compromised patient information, and legal ramifications for healthcare organizations.
How can organizations ensure compliance with HIPAA regulations?
Organizations can ensure compliance by conducting regular risk assessments, implementing security measures like encryption, training staff on data security protocols, and maintaining audit trails.
Why is network segmentation important in a healthcare cloud environment?
Network segmentation helps isolate sensitive data, restrict access only to authorized personnel, and contain potential security breaches within specific segments of the network.