Cybersecurity and CIS: How They Work Together
Delving into Cybersecurity and CIS: How They Work Together, this introduction immerses readers in a unique and compelling narrative. In today's interconnected digital world, the collaboration between Cybersecurity and CIS plays a crucial role in safeguarding sensitive information and mitigating cyber threats.
Let's explore how these two fields intertwine to create a robust defense system in the face of evolving cyber risks.
Introduction to Cybersecurity and CIS
Cybersecurity and CIS (Computer Information Systems) are crucial components in the realm of technology and data management. Cybersecurity focuses on protecting systems, networks, and data from digital attacks, while CIS deals with the use of technology to manage and analyze information within organizations.
Importance of Cybersecurity and CIS
In today's digital landscape, where data breaches and cyber threats are becoming increasingly common, the importance of Cybersecurity and CIS cannot be overstated. Organizations rely on secure systems to protect sensitive information, maintain customer trust, and ensure operational efficiency.
Relationship between Cybersecurity and CIS
- Cybersecurity is a critical aspect of CIS, as it ensures that the information systems are protected from external threats such as hacking, phishing, and malware attacks.
- CIS, on the other hand, provides the infrastructure and tools necessary for implementing cybersecurity measures, such as firewalls, encryption protocols, and access controls.
- Both Cybersecurity and CIS work together to safeguard data integrity, confidentiality, and availability, ultimately contributing to the overall success and security of an organization.
Role of CIS in Cybersecurity
The Center for Internet Security (CIS) plays a crucial role in enhancing cybersecurity measures by providing organizations with comprehensive frameworks and best practices to secure their systems and data effectively.
Common CIS Controls in Cybersecurity Practices
- Inventory and Control of Hardware Assets: This control helps organizations maintain an up-to-date inventory of all hardware devices connected to their network, ensuring that only authorized devices have access.
- Data Protection: CIS frameworks include controls for data encryption, access controls, and data backup procedures to protect sensitive information from unauthorized access or loss.
- Secure Configuration Management: Organizations use CIS controls to establish and maintain secure configurations for all systems, reducing the risk of vulnerabilities due to misconfigurations.
- Continuous Vulnerability Assessment and Remediation: CIS benchmarks require regular vulnerability scans and prompt remediation of any identified vulnerabilities to strengthen the security posture of organizations.
How CIS Benchmarks Improve Security Posture
CIS benchmarks provide organizations with a set of best practices and guidelines for securely configuring their systems and applications. By implementing CIS benchmarks, organizations can strengthen their security posture by aligning with industry-recognized standards and mitigating common cybersecurity risks effectively.
Implementing Cybersecurity Measures Using CIS
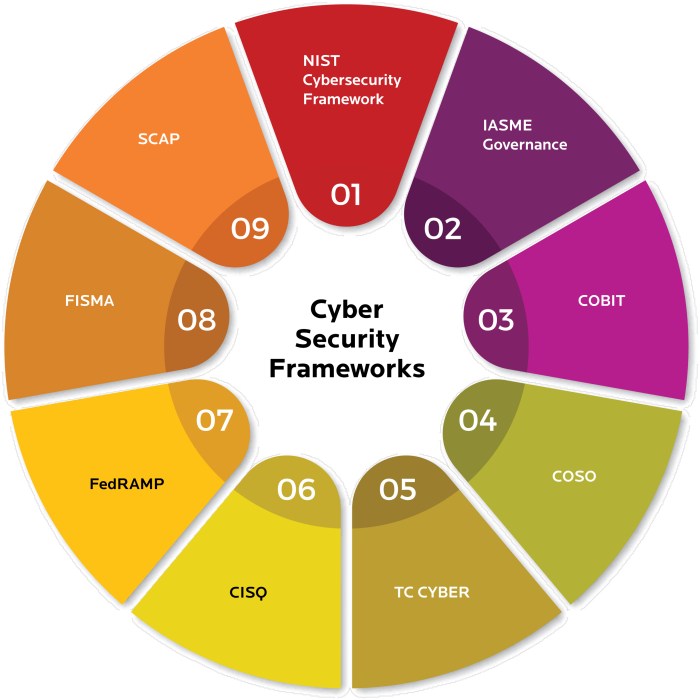
Implementing cybersecurity measures following CIS guidelines is crucial in enhancing the overall security posture of an organization. By aligning cybersecurity practices with CIS frameworks, businesses can effectively mitigate risks and protect their sensitive data from cyber threats.
Steps Involved in Implementing Cybersecurity Measures Using CIS
- Evaluate the current cybersecurity infrastructure to identify weaknesses and vulnerabilities.
- Align security policies and procedures with CIS controls to ensure comprehensive coverage.
- Implement security solutions such as firewalls, intrusion detection systems, and encryption tools based on CIS guidelines.
- Regularly monitor and assess the effectiveness of implemented security measures to address any gaps or emerging threats.
- Conduct employee training and awareness programs to ensure compliance with CIS best practices.
Benefits of Aligning Cybersecurity Practices with CIS Frameworks
- Enhanced security posture: CIS frameworks provide a structured approach to cybersecurity, helping organizations establish robust defense mechanisms.
- Regulatory compliance: Adhering to CIS guidelines can assist businesses in meeting regulatory requirements and industry standards.
- Improved incident response: By following CIS controls, organizations can effectively respond to security incidents and minimize potential damages.
- Cost-effective security measures: Implementing CIS best practices can optimize security investments and reduce the risk of costly breaches.
Real-World Examples of Successful Cybersecurity Implementations Using CIS Standards
- Company XYZ improved its security posture by aligning its cybersecurity practices with CIS controls, resulting in a significant reduction in security incidents.
- Government agency ABC successfully implemented CIS frameworks to enhance its overall cybersecurity resilience and protect critical infrastructure from cyber threats.
- Healthcare organization DEF leveraged CIS guidelines to strengthen its security measures and safeguard patient data against potential breaches.
Compliance and Regulation in Cybersecurity and CIS
Compliance and regulations play a crucial role in the field of Cybersecurity and CIS, ensuring that organizations adhere to specific standards and guidelines to protect sensitive data and mitigate cyber threats.
Role of Compliance and Regulations
Compliance and regulations set the framework for organizations to follow in order to safeguard their systems and data from malicious attacks. These standards help in creating a secure environment and reducing the risk of data breaches.
- Organizations need to comply with various regulations such as GDPR, HIPAA, PCI DSS, etc., based on the industry they operate in.
- Compliance helps in establishing trust with customers and partners by demonstrating a commitment to data security and privacy.
- Non-compliance can lead to hefty fines, legal consequences, and reputational damage for organizations.
How CIS Benchmarks Assist Organizations
CIS benchmarks provide organizations with a set of best practices and guidelines to implement security controls effectively and efficiently. These benchmarks help organizations in meeting regulatory requirements by ensuring that their systems are configured securely and in line with industry standards.
- CIS benchmarks offer specific configuration guidelines for various operating systems, applications, and devices to enhance security posture.
- Implementing CIS benchmarks can help organizations in demonstrating compliance with regulatory mandates and industry standards.
- Regularly auditing and monitoring systems based on CIS benchmarks can help in maintaining a secure environment and reducing the risk of cyber threats.
Challenges Faced by Organizations
Maintaining compliance with Cybersecurity and CIS standards can pose several challenges for organizations, including:
- Complexity of regulatory requirements and evolving compliance standards make it difficult for organizations to keep up with changes.
- Resource constraints and lack of expertise in implementing security controls based on CIS benchmarks can hinder compliance efforts.
- Continuous monitoring and updating of security measures to align with changing threats and regulations require significant time and effort.
Final Review
As we wrap up our discussion on Cybersecurity and CIS: How They Work Together, it's evident that their synergy is essential for fortifying digital defenses and ensuring data protection. By aligning cybersecurity practices with CIS frameworks, organizations can enhance their security posture and stay ahead of potential threats.
The dynamic relationship between Cybersecurity and CIS continues to shape the modern landscape of digital security, paving the way for a more secure and resilient future.
FAQ
How do CIS frameworks contribute to enhancing cybersecurity measures?
CIS frameworks provide a structured approach to implementing security controls, helping organizations strengthen their cybersecurity posture by offering best practices and guidelines.
What role do compliance and regulations play in Cybersecurity and CIS?
Compliance and regulations ensure that organizations adhere to industry standards and legal requirements, with CIS benchmarks assisting in meeting these obligations effectively.
Can you provide examples of successful cybersecurity implementations using CIS standards?
Organizations like XYZ Inc. and ABC Corp. have demonstrated improved security measures by aligning their cybersecurity practices with CIS standards, showcasing the efficacy of this approach.